Overview
Unqork's security best practices are important for building applications using the Unqork Designer Platform. Follow the best practices listed below if your application captures sensitive data (PII), uses schema modules to store submission data, contains external integrations using API (Application Programming Interface) calls, or opens API modules for external access.
Application configuration security best practices covers modules, components, and workflows.
General Configuration Best Practices
Data Collections
Data collections are static data tables referenced by application modules. The data collections can be accessed either server-side, client-side, or both.
To learn more about data collections, visit our Workspaces: Working with Reference Data article.
Best practices for data collections include:
Avoid storing sensitive data such as API keys or passwords in data collections.
Enable Server Side Execution Only for server-side only collections. Server side execution prevents processed data from being exposed in Express View.
Privilege Escalation
Privilege escalation flaws let end-users elevate access and gain access to protected data. The privilege escalation vulnerability is common in software applications including ones built by no-code platforms.
Common mistakes leading to potential privilege escalation vulnerabilities in an Unqork application include:
RBAC misconfiguration.
Granting excessive permission with the Full Submission setting lets users of that role to access all submission data.
API/modules return data to client/browser without applying a filter when executing server-side as a super user.
Excessive permissions to schema modules that lead to access all submissions using API.
Excessive permissions to workflow application modules that lead to access all workflow submissions using API.
To prevent privilege escalation:
Design strong RBAC controls for applications.
To learn more about implementing RBAC (Role-Based Access Control), visit our Introduction to Role-Based Access Control (RBAC) For Express View article.
Avoid turning on Full Submission for User roles.
Filter returning data from API modules.
Enable server-side execution for schema modules and avoid turning on Act as super-user when server-side executing.
Use the
currentUserobject for user details like Name and Role in a server-side module. Avoid passing the username, role, and email parameters from the browser.
Input and Data Validation
Application misconfiguration lets users bypass input validation to save/access data, including:
Manipulating URL query parameters when server-side validation is misconfigured or missing.
Replaying API requests to save the same data multiple times. APIs can be replayed using "man in the middle" tools or capturing requests using browser developer tools.
Bypassing Enable/Disable action buttons based on user input.
Inspecting and editing HTML attributes using browser developer tools.
To prevent input/data validation vulnerabilities
Add validation before module submission requests that are executed by the client or browser.
When possible, validate data in a server-side module.
Module Best Practices
Act As Super-User When Server Side Executing
The Act as Super-user when Server Side Executing setting grants non-administrative users privilege to run as an administrative user with full access to submissions including the submissions the current users don’t have access to.
To learn more about Server-Side execution, visit our Server-Side Module Execution article.
Use a proxy module (with proxy pattern) to execute modules with server-side execution.
To learn more about proxy patterns, view our Proxy Module Validation Pattern article.
Apply data filters before returning the data to the client/browser.
Using the Other Module Type and Connecting to External APIs
Create schemas using the O modules with the following settings:
Tag the module with the keyword
api. Tagged modules are accessible in the API Docs Dashboard Tool.Enable Server-side Execution Only in the module setting for external API service endpoints that are configured in server administration.
Enable Customize RBAC for this Module in module permissions.
Disable Allow Access to Anonymous Users in module permissions.
To learn how build API modules, visit our API Specification Snippet article.
Empty Modules
Modules can be saved with no components in them. There is no security risk with empty modules but it is best practice to remove empty modules from an environment.
Imported Module References
Remove all references to a deleted module. If you delete an imported module, the references to the deleted imported module are not automatically deleted. References to deleted imported modules can cause runtime issues.
Modules in an Automated Workflow
Create modules in the Automated Workflow lane with the following settings:
Enable Server-side Execution Only in
.png) Module Settings for external API service endpoints that are configured in server administration. SSE prevents external services from seeing sensitive information such as financial data or PII (Personal Identifiable Information).
Module Settings for external API service endpoints that are configured in server administration. SSE prevents external services from seeing sensitive information such as financial data or PII (Personal Identifiable Information).Enable Customize RBAC for this Module in the module permissions.
To learn more about Automated Workflows, visit our Swimlane Management article.
Module With Anonymous User Access
Modules enabled for anonymous users with module permission setting Access to Anonymous Users are accessible without authentication.
Limit modules with anonymous user access including login and homepages.
Avoid accessing sensitive data or execute external APIs in modules with anonymous user access.
Schema Modules
The Schema module defines properties of a submission, access to them, and how they relate to other submissions within an application.
To learn more about using schema modules, view our Schema Docs Dashboard Tool article.
Create schema modules with the following settings to improve security:
Tag the Schema module with the keyword schema. Schema tagged modules are accessible in the Schema Docs Dashboard Tool.
For O modules, enable the Server-side Execution Only (SSE) in
.png) Module Settings. SSE prevents users from accessing sensitive data stored module.
Module Settings. SSE prevents users from accessing sensitive data stored module.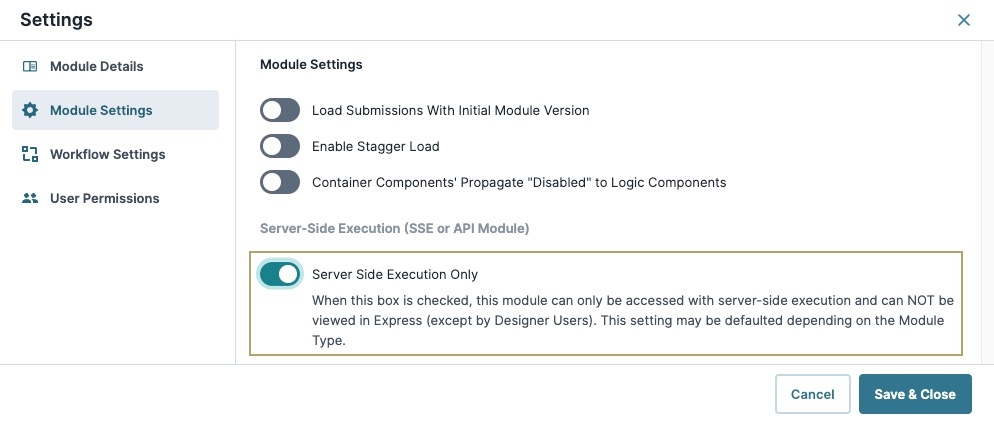
Disable Act as Super-User when server-side executing in the
.png) Module Settings.
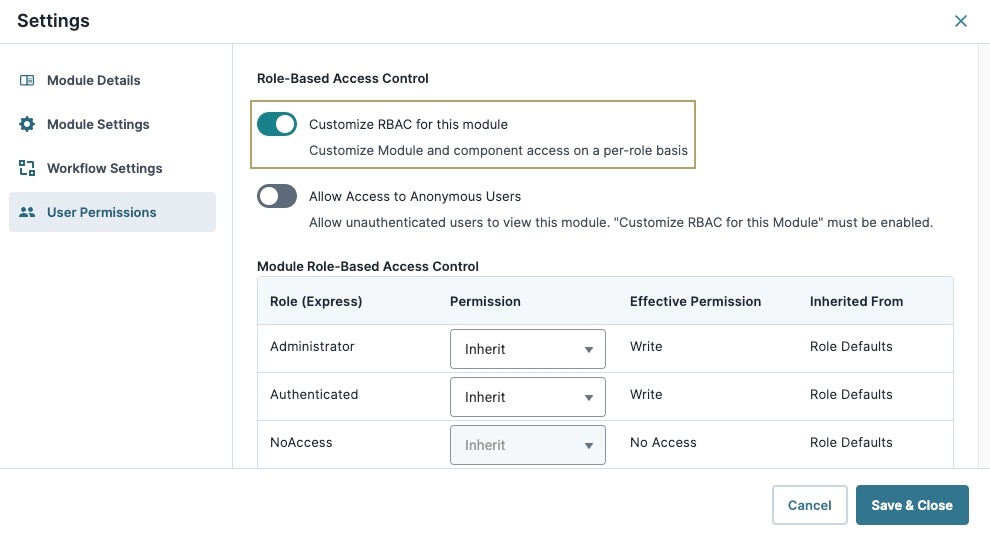
Module Settings.Disable Allow Access to Anonymous Users in User Permissions.
Enable Customize RBAC for this Module in User Permissions.
Components and Operators Best Practices
File Component
Avoid using * for the file formats. Instead, specify file acceptable formats like .pdf, and .jpg. Limiting formats prevents executables, scripts, and other potentially malicious content from uploading to your application.
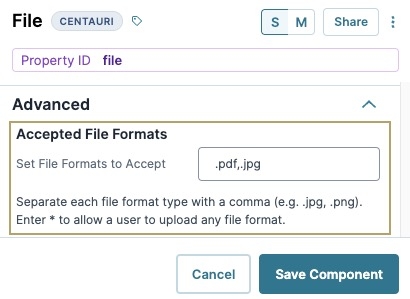
Set the maximum file upload size. Restricting file size prevents unexpectedly large files from causing your application to fail.
To learn more about the File component, visit our File Component article.
File Storage Component
Use the SFTP file storage type, don’t use FTP. SFTP provides additional security during the data transfer process.
Unqork only supports the FTP file storage type for legacy system file transfers that are unable to use SFTP.
Enable Server-side Execution Only for the services used in the File Storage component. Enabling SSE prevents the exposure of sensitive information.
To learn more about the File Storage component, visit our File Storage Component article.
Data Workflow HTML Table Operator
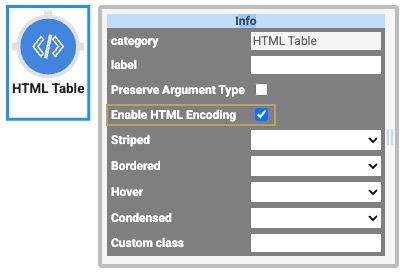
Enable the Enable HTML Encoding setting to prevent code snippets in user input execution. HTML Encoding helps mitigate vulnerabilities like XSS (Cross-site scripting) injections.
To learn more about the HTML Table operator, visit our HTML Table Operator article.
Excel Export
A common use case is to export data as an Excel file. To implement the Excel export functionality, convert table data to HTML in a Data Workflow and using an HTML table in the Content component.
Encode data before using it in an Excel export.
In an HTML Table operator, set Enable HTML Encoding to
.png) (checked) when data is used in an Excel export. HTML Encoding helps mitigate vulnerabilities such as XSS (cross-site scripting) injections.
(checked) when data is used in an Excel export. HTML Encoding helps mitigate vulnerabilities such as XSS (cross-site scripting) injections.Avoid using safehtml in Content components. For example:
<span ng-bind-html="data.excelData | safehtml">.