Overview
Applying administrative best security practices is important when managing a workspace. Improper administrative settings might lead to PII (personal identification information) becoming exposed, or allow outsides sources to capture private information from your applications. To improve your workspace security, integrate Unqork's best practices for administrative settings.
Express Role Administration
The Express Role Administration page lets you create Express roles and set their hierarchy. Below is a glossary of best security practices for Express Role settings.
To learn more about Express Role administration, visit our Express Role Administration article.
Excessive Permissions
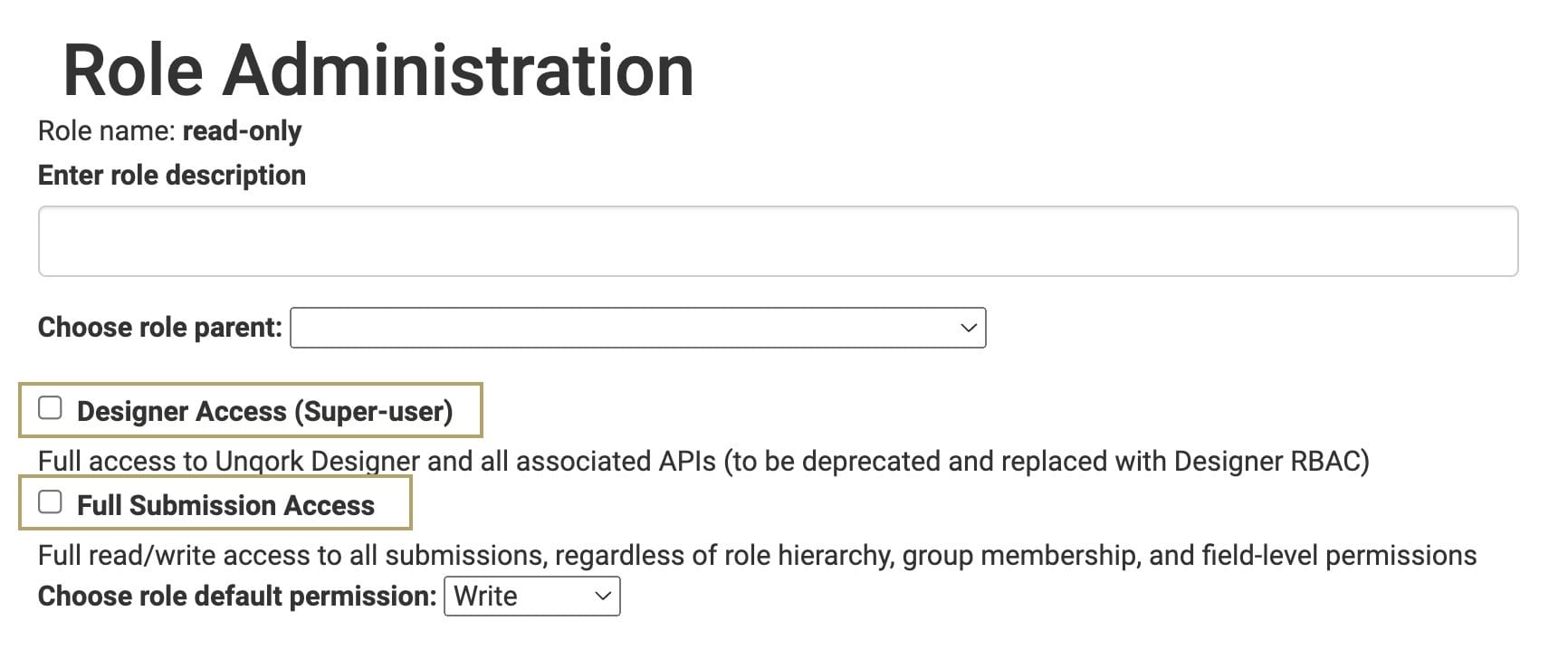
Granting end-users Designer and Full submission access allows them to browse data from all submissions. Keep these best practices in mind to avoid excessive permissions:
Designer Access (Super-user): When selected, users have full access to the Unqork Designer and all related APIs. End-users with the Designer Access permission can also modify or delete modules. We recommend that you disable Designer Access for express roles. Rather, use the Designer User role when assigning designer access.
Full Submission Access: When selected, Full Submission Access overrides all other permissions. User roles with Full Submission Access can read all submission data. It's recommended that you limit Full Submission Access to necessary roles only.
Environment Administration
Environment Administration is where you can customize environment-related settings. Below is a glossary of Environment Administration settings and best security practices.
To learn more about environment administration, visit our Environment Administration article.
API Rate Limiting
Improve integration security by limiting the API (application programming interface) rate. In the API Rate Limiting settings section, you have the option to select a limiting rate. Here, you can limit the number of API requests from any single IP per server per 60 seconds.
The smallest number of requests you can enter is 100, while the largest is 1,000,000. But, it's recommended to set this to a lower number. By setting your limit to a lower number, you reduce the likelihood of automated attacks.
The API Limiting setting helps protect against many Automated attacks. These include brute-force searches, enumerations, or HTTP request flooding.
Express Session Administration
Enforce a strong session management policy. Do this by implementing two changes to the Express Session Administration setting section:
Select Expiration on Browser Quit from the Expire User Sessions in Express drop-down menu. By selecting this option, you set all browser cookies to session cookies. Once the browsing session ends, your browser automatically deletes session cookies.
Set your Session Timeout to a lower number. Setting a shorter amount of time for the session to timeout increases security. It does this by reducing the likelihood and amount of time a malicious actor can use a stolen session.
Server Side Execution Request/Response Body and Debug Logs
The configuration setting Server Side Execution Request/Response Body Log enables logging of the request and response body for all the server-side execution modules.
In production environments, disable logging by selecting the option Do not capture request/response bodies. This prevents logs from capturing and storing PII (personally identifiable information) data.
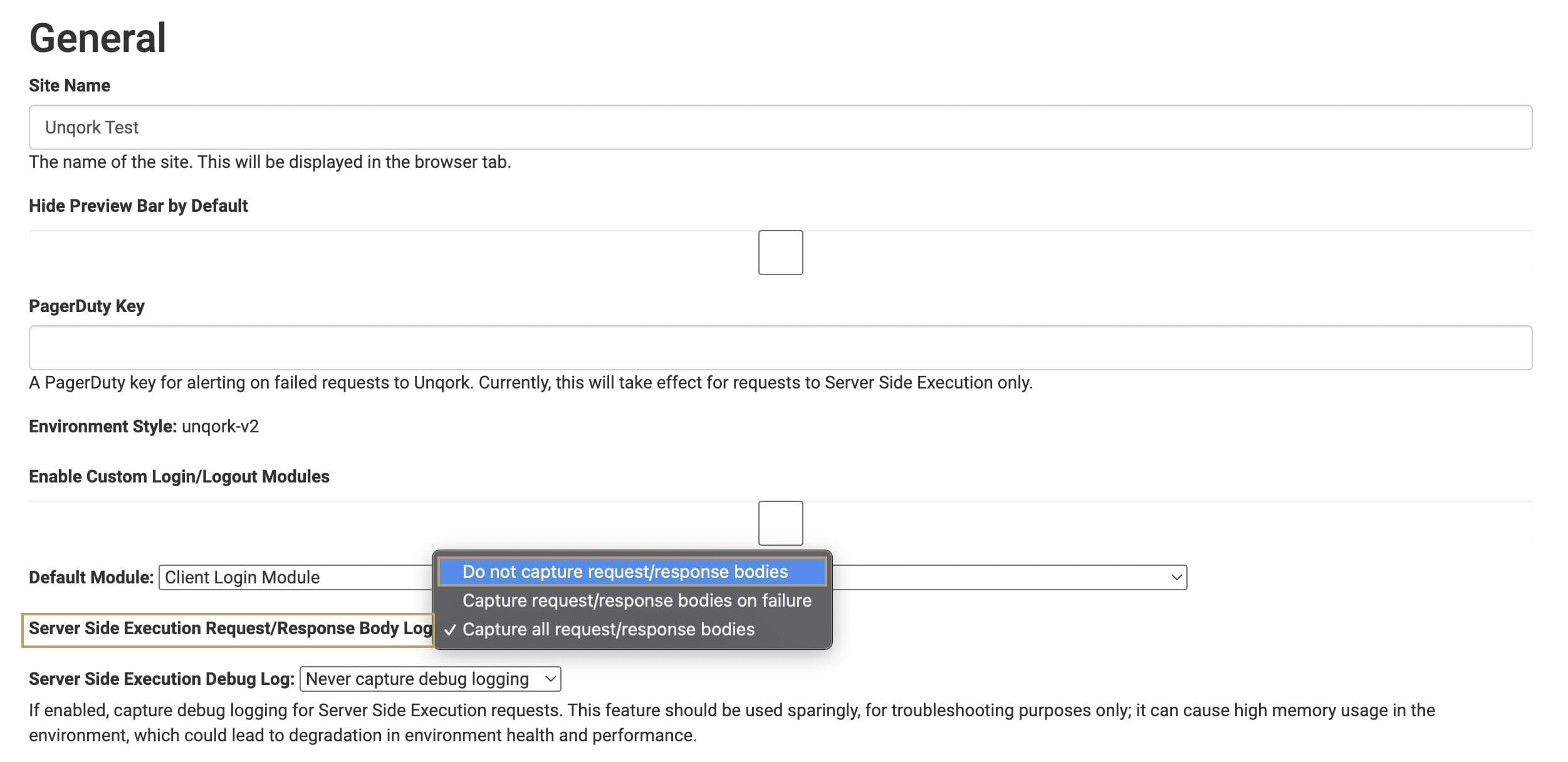
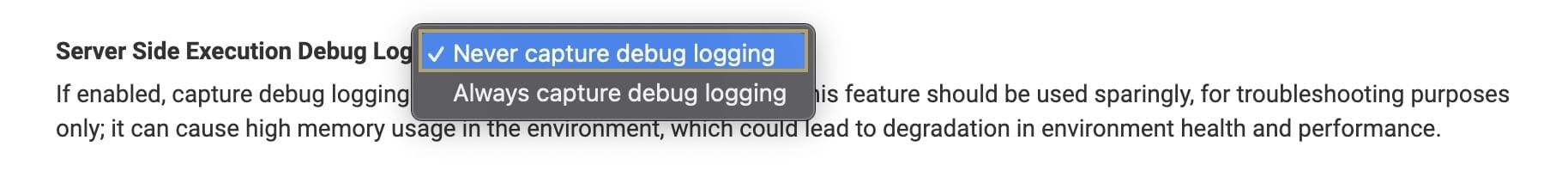
When debugging, enable Always capture debug logging to capture logs for troubleshooting, then turn the setting off once the debugging is finished.
Enable OAuth2 Password Grant
Disable the Enable OAuth2 Password Grant setting for all users. Create a dedicated express service user for API access. Disabling this setting prevents phishing attacks and increases security for users.
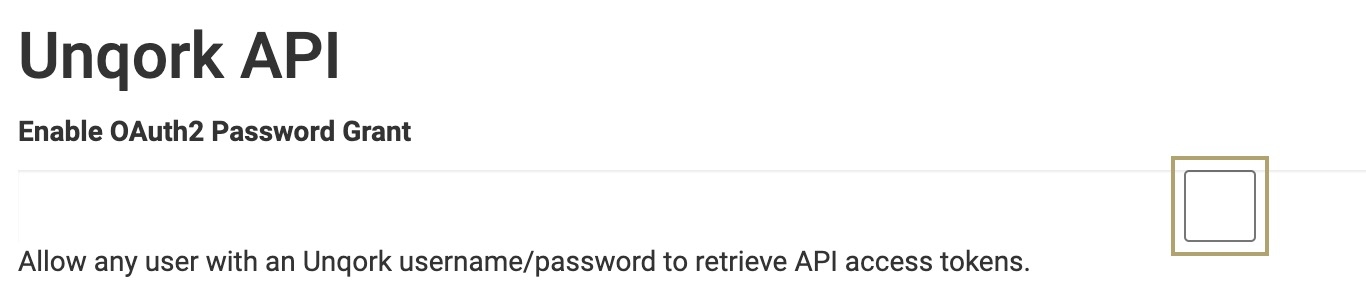
Environment Administration Strong Password Requirements
Enforce a strong password policy in all environments. A short or weak password is vulnerable to brute-forcing or password spraying attacks.
In Password Requirements, set a minimum password length of at least 12 characters. The default setting for the minimum password length is eight characters.
In Password Requirements, select the following checkboxes: Require Lowercase Letter, Require Uppercase Letter, Require Number, and Require Symbol.
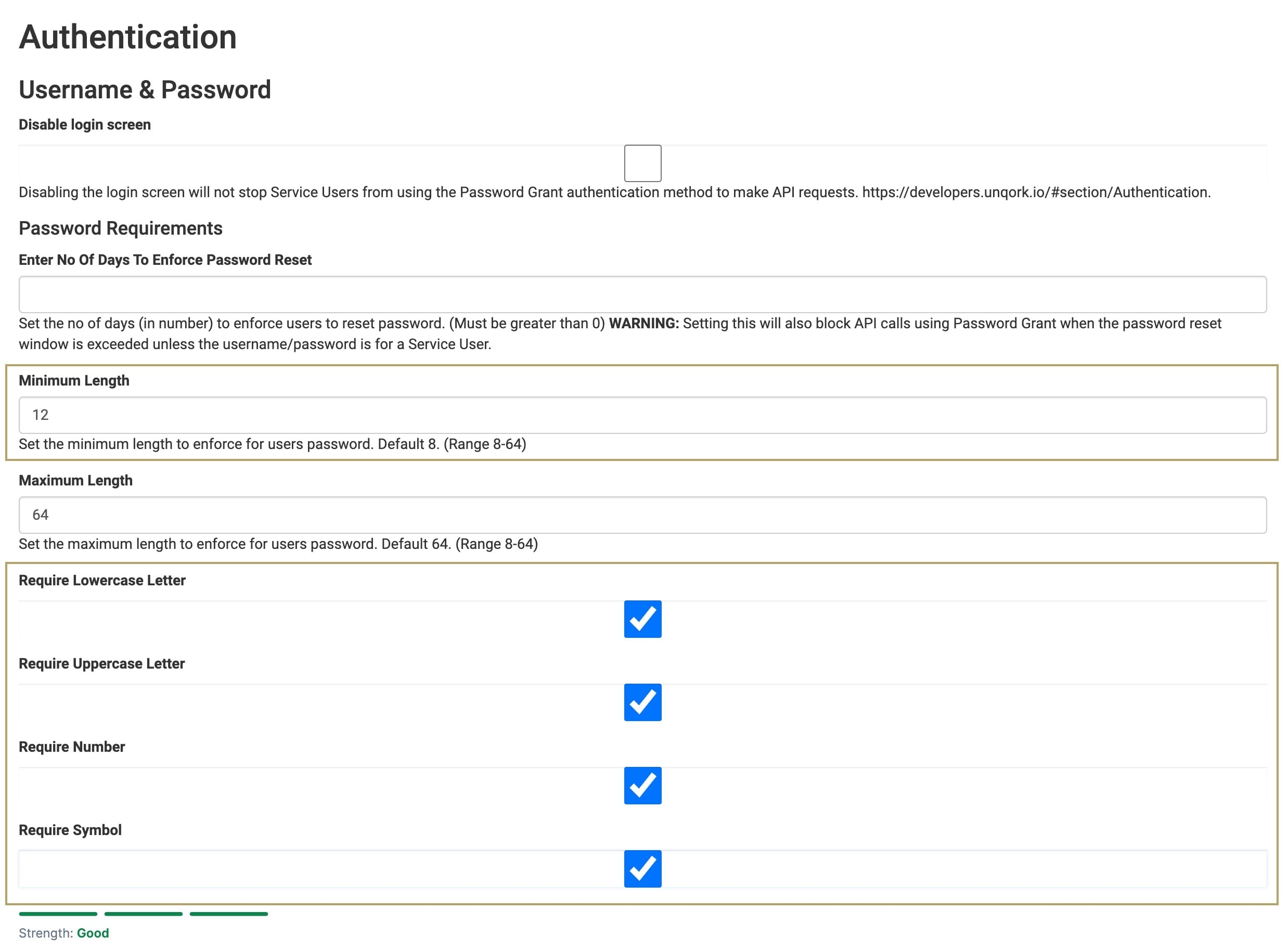
Express User Session Expiration in Browser
Enable Expiration on Browser Quit. This option prevents unauthorized access by removing the end-user's cookies and setting the session to expire when the end-user closes their browser.

Inactivity and Session Timeouts
From the Expire User Sessions in Express drop-down, select Expiration on Browser Quit. This removes the session when the browser is closed.
Set Inactivity Timeout and Session Timeout to a smaller window. Unattended accounts with active tokens can be taken advantage of by attackers. Consider company guidelines and policies to configure timeout values.
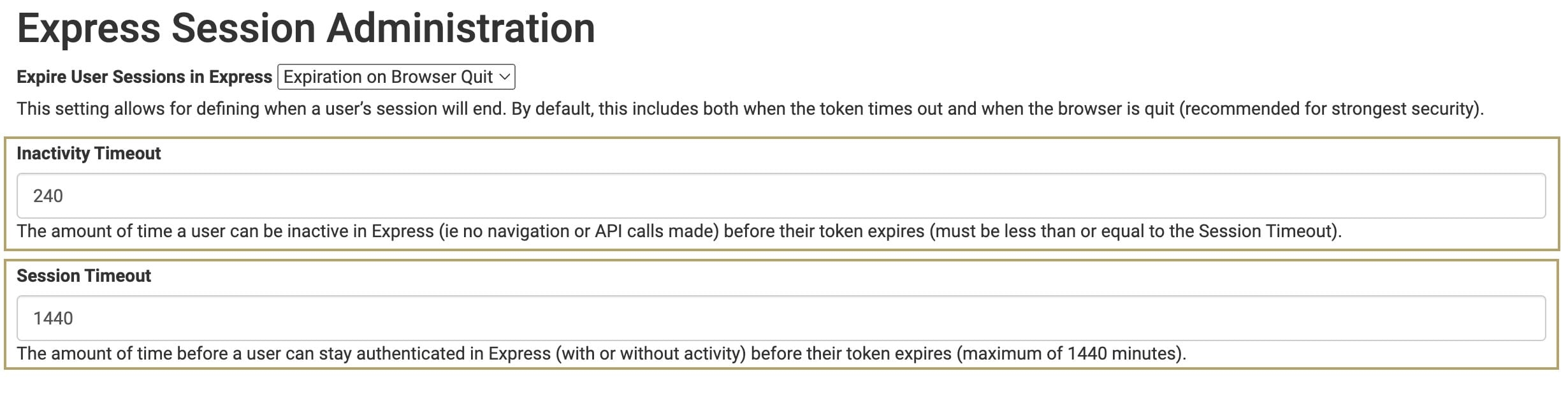
Global Variables
A global variable is a named identifier (or key) that is paired with a value. Common use cases for global variables are to reference the same value in multiple modules or components for environment (stage/UAT) specific values.
Avoid using external API keys or secrets in global variables.
Enable Sever-Side only for global variables used in server-side execution modules. Server-Side only prevents clients and browsers from accessing global variables.
To learn more about global variables, visit our Global Variables Administration article.
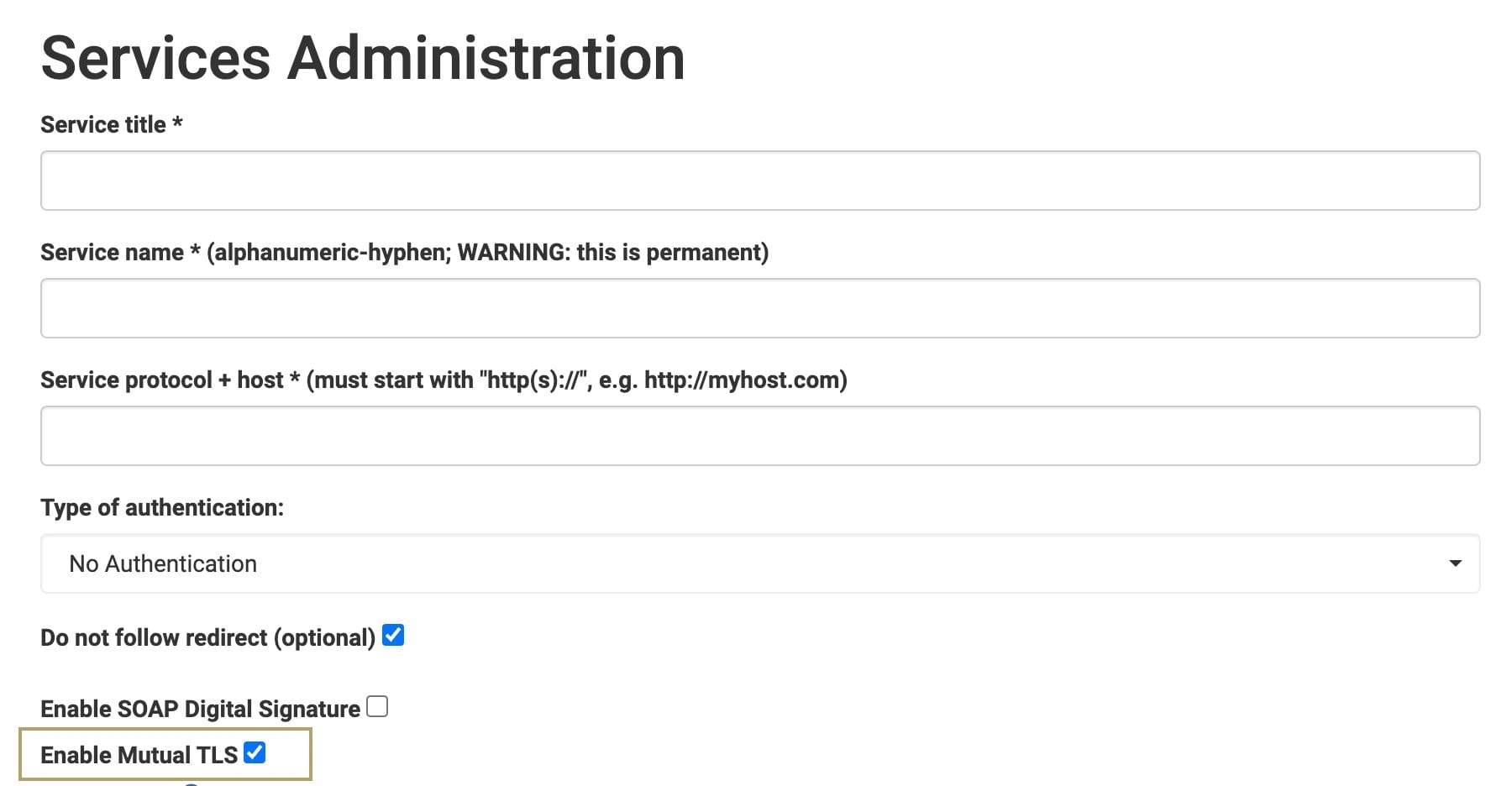
Services Administration
Services Administration stores authentication details and sensitive information like keys and pass-phrases. While you can't view or access this information when configuring a module, you can use it in a Plug-In component. Store keys and pass-phrases in Services Administration so they're never exposed to end-users in deployed applications.
To learn more about Services administration settings, visit our Services Administration article.
Authenticate Services
When setting up new services, always authenticate if possible. Authenticating services proves that the service is genuine and won't pose a threat to your application.
To learn more about API authentication, view our API Authentication article.
Store API Keys in a Secure Location
Do use API keys to authenticate your API service calls. With these keys, you can track and control how end-users use your API. To prevent malicious actors from accessing these keys, store them in a secure yet accessible location.
Another way to secure API keys is to not use the same keys across different environments. Avoid using the same API keys for production and non-production environments.
Encrypt Communication
Encrypt all channels of communications between the client and the server. Encrypting communication prevents eavesdropping, tampering, and message forgery.
Use TLS (transport layer security) to encrypt communications. TLS increases the security of your application's communications. TLS provides a necessary transport layer of protection that guarantees confidentiality, integrity, authentication, and replay prevention.
When setting up communications, use an encrypted channel such as TLS for all communications.
Avoid Exposing Sensitive User Objects
When you perform integrations with your application, you might expose end-user object attributes. As you make these exposures in Services Administration, be mindful of what's exposed to external services. For example, avoid storing sensitive information in end-user custom attributes. Services Administration might expose Custom attributes. That's because attributes exposed in Services Administration could expose to external services.
Logging Capture Request & Response Bodies
In production environments, disable the Logging Capture request & response bodies setting to prevent sensitive data (PII, financial) from being captured.
The option Logging Capture request & response bodies is specific to each server configuration. Disable the Logging Capture request & response bodies for all services.
Insecure HTTP Protocol in Use
Avoid using HTTP and FTP protocols. When adding services to Unqork, use HTTPS (Hypertext Transfer Protocol Secure) and SFTP (Secure File Transfer Protocol).
Enable Mutual TLS
Enable Mutual TLS (Transport Layer Security) when external services support it. Mutual TLS ensures data is encrypted, secure, and trusted between client and server.