Overview
mLTS (Mutual Transport Layer Security) certificates add an extra layer of security on top of other integrations. You can link mTLS certificates to most service authentication types available on the Services Administration page. To add certificates to your environment, though, you'll use Certificate Management.
Some authentication types don't support using mTLS certificates. These include: Canada Post, Decryption (GPG), Encryption (GPG), FTP, Google Places, HMAC, Plaid, SFTP, and Twilio.
From Certificate Management, you can easily add, view, and manage mTLS certificates in your environment. After adding a certificate to your environment, you have a few options for how and where to link services to the certificate. In this article, you'll see how to link a certificate to a service when adding the service in Services Administration.
These instructions assume you already added the certificate to your environment's Certificate Management page. Learn how to add certificates using our Certificate Management.
Adding an OAuth 2.0 Authentication Service to Services Administration
Let's start by setting up the OAuth 2.0 authentication service. Here, you'll use the OAuth2 Client Credentials Grant authentication type.
At the top right of the Unqork Designer Platform, click the Administration button.
Under Integration, click Services Administration.
Click + Add a Service
In the Service Title enter
OAuth2 + mTLS Certificate.In the Service Name field, enter
OAuth2mTLS Certificate.The Service Name value is permanent and cannot be changed.
Click Next. The Manage Access tab displays.
Set Share to to Environment.
Click Create. The SendGrid services page displays.
Click Edit
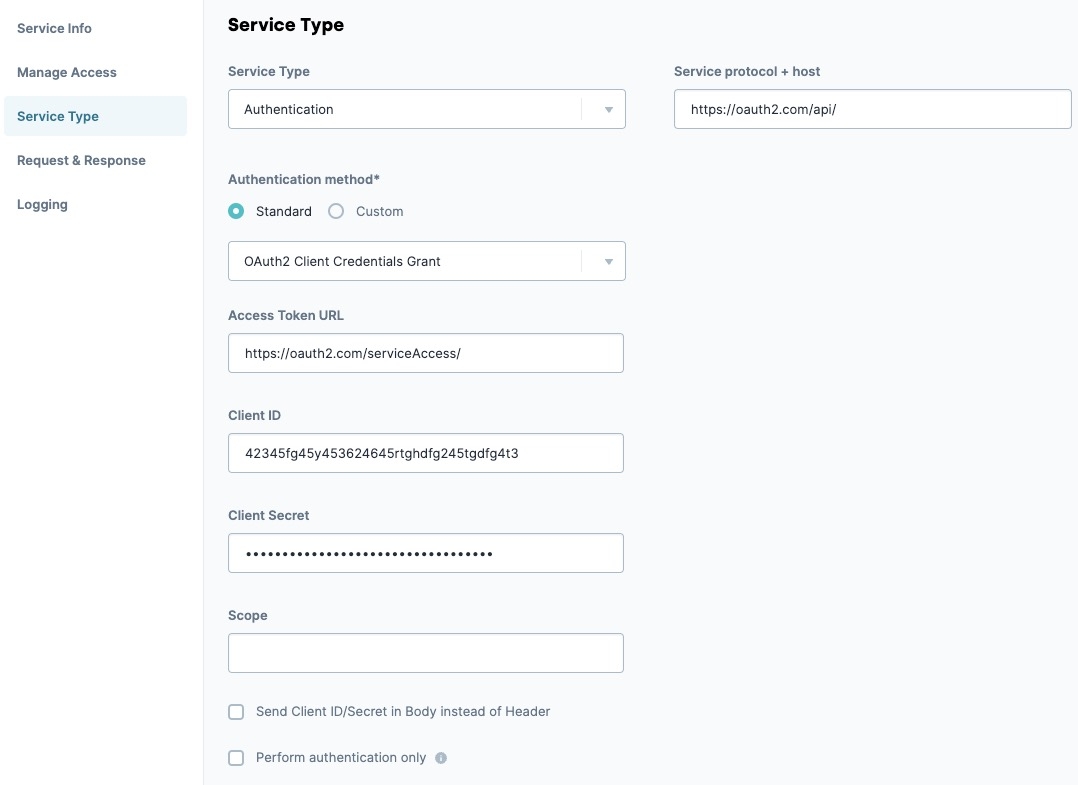
From the navigation menu, select Service Type.
In the Service Protocol + Host field, enter the service protocol address.
Under Authentication Method* from the drop-down, select OAuth2 Client Credentials Grant.
After selecting the Type of Authentication, prompts appear for more information. Different authentication types have different setup needs. For example, in the case of OAuth2 Client Credentials Grant, you'll see the following fields: Access Token URL, Client ID, Client Secret, and Scope.
Enter the access token in the Access Token URL field.
Enter the client ID in the Client ID field.
Enter the client secret in the Client Secret field.
If required, enter the scope in the Scope field. This field is optional.
Adding an mTLS Certificate to an Authentication Service
Next, you'll use the Enable Mutual TLS setting to link the mTLS certificate to your service. You can follow these steps to add an mTLS certificate to any service that supports it.
Set Enable Mutual TLS to
.png) (checked).
(checked).From the Certificate drop-down, select a certificate.
Click Save Changes.