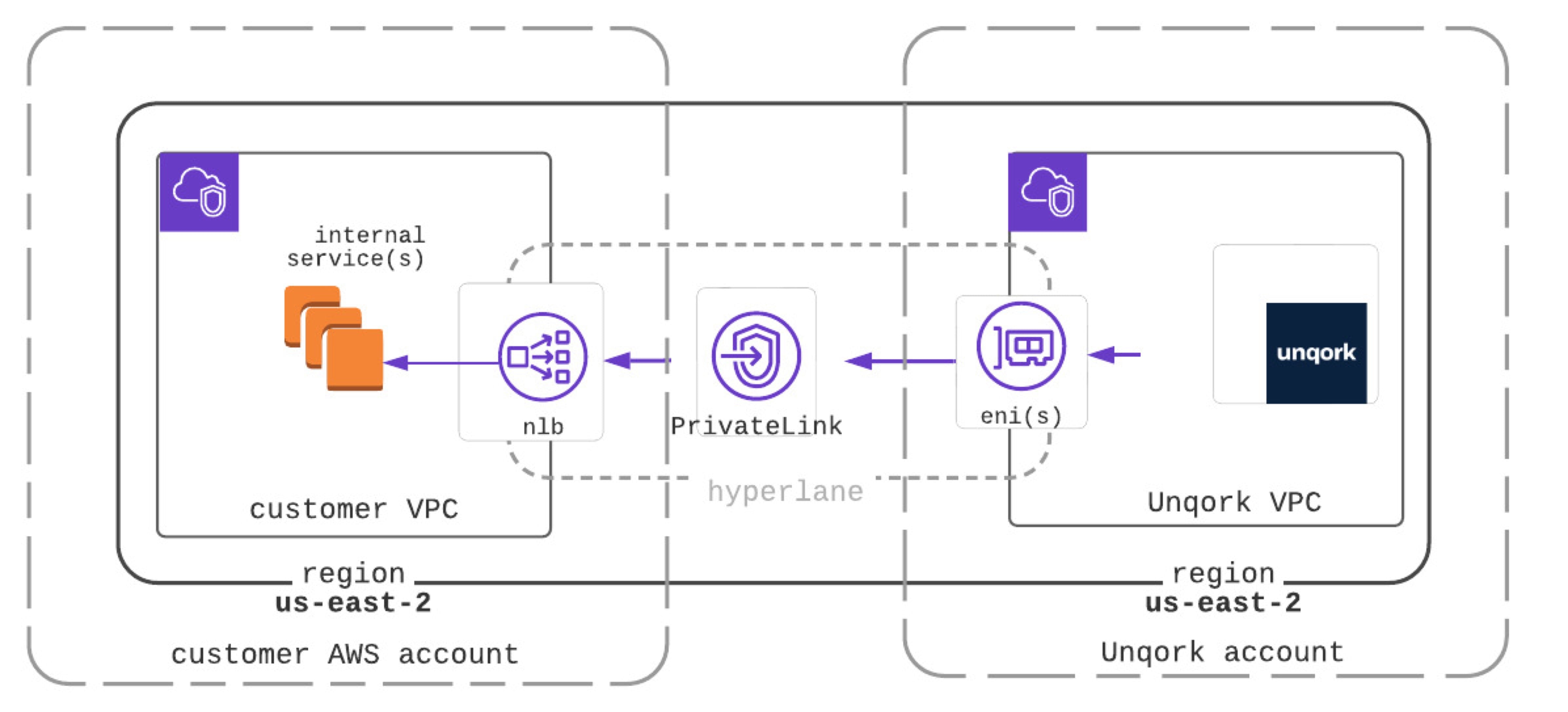
Overview
Setup AWS PrivateLink to connect two VPCs (virtual private clouds) in different AWS accounts. The first is a VPC in your AWS account, the second is the dedicated VPC where your Unqork environment exists. If your AWS resources are connected to on-premises networks, the Unqork services can also interact with services in your data center. Similarly, Unqork services can interact with services in your other VPCs if they are peered.
AWS PrivateLink as a secure tunnel, keeping your traffic safe without traversing the public internet. Typically, services communicate from one endpoint to another. With AWS PrivateLink, communication travels from your endpoint service to a VPC endpoint in your hosted Unqork environment. The endpoint service using PrivateLink works with a network load balancer (NLB), acting as an entry point to your infrastructure. Because you create the VPC endpoint in AWS, you don’t need any other hardware or software.
How AWS PrivateLink Works in Unqork
Unqork acts as the service consumer and your endpoint service acts as the service owner. Unqork initiates the connection to a resource in your cloud account. After initiating the connection, the service provider can respond to requests from Unqork. You'll need to generate the private domain using Unqork and set up an external service integration. In your VPC, the same region as your Unqork environment, you’ll set up the endpoint service. That endpoint service is then configured in a Plug-In component to forward traffic to the NLB.
How to Set Up AWS PrivateLink
To set up AWS PrivateLink, you'll first configure settings in Unqork and AWS. Then, you’ll set up a Plug-In component in Unqork and connect to the service.
What You Need
In your AWS account, you need:
Identity and access management (IAM) role privileges to create and manage VPCs, endpoints, and endpoint services.
A VPC in the same region as your Unqork environment.
VPC subnets where the target resources reside.
NLB configured for each subnet, with cross-zone load balancing enabled.
An endpoint service, or the PrivateLink.
The endpoint service name from AWS.
In Unqork, you need:
1 Initializer component.
1 Plug-In component.
The Amazon Resource Name (ARN) from your Unqork Environment.
Copy the Unqork ARN (In Unqork)
Before you begin, copy the ARN from your Unqork environment. You'll need the ARN later to configure your NLB.
At the top right of the Unqork Designer Platform, click Administration.
Under Integration, select PrivateLink Administration.
Copy the ARN of your environment.
You'll allow traffic to originate from this ARN in the Create the Endpoint Service section of this article.
Create an Endpoint Service for Your AWS PrivateLink (In AWS)
Next, set you'll set up your endpoint service and NLB in AWS.
Configure the VPC Endpoint Service and NLB
First, set up your VPC endpoint service and NLB.
The resource does not need to be in the same region. If there are multiple resources in different regions, you’ll set up VPC Peering to the VPC in the same region as Unqork.
In AWS, select or create a VPC.
Configure the VPC to include subnets in each availability zone (AZ).
On the AWS Console's EC2 page, select or create a load balancer.
Configure the NLB with the following settings:
Setting
Value
Load Balancer Name
Enter a name for the load balancer.
The name must be unique. Once created, you cannot edit the name.
Scheme
Select Internal.
VPC
From the drop-down, select the VPC you want to use.
Listeners and Routing
Forward to: select or create a target group.
Your internal load balancer must have a private subnet.
After you create your NLB, configure it with the following settings:
Setting
Value
Cross-Zone Load Balancing
Select Enabled.
This setting is necessary so Unqork's network interfaces connect with your resources. Enable this setting even if your subnets do not share AZs with Unqork.
Require Acceptance for Endpoint
Select Acceptance Required. We recommend this setting for production use.
For more information on NLBs, view the AWS documentation: https://docs.aws.amazon.com/elasticloadbalancing/latest/network/introduction.html.
Create the Endpoint Service
Now, create the endpoint service in AWS.
Under the AWS Console's Virtual Private Cloud (VPC) page, go to Endpoint Services.
Select the Allow Principals tab.
Click Allow Principals.
Paste the ARN you copied in the Copy the Unqork ARN section of this article.
Click Add Principal.
Click Allow Principals.
The Service name does not exist error displays if you do not select Allow Principals.
To learn more about AWS PrivateLink endpoint service configuration, view the AWS documentation: https://docs.aws.amazon.com/vpc/latest/privatelink/endpoint-services-overview.html.
Copy the AWS Endpoint Service Name (In AWS)
Next, copy the AWS endpoint service name that you created to set up the AWS PrivateLink connection.
The endpoint service configuration makes the PrivateLink in AWS.
In AWS, go to Endpoint Services.
Select the endpoint service that you created in the Configure the VPC Endpoint Service and NLB section of this article.
Under Details, copy the Service Name. This endpoint service acts as the AWS PrivateLink in your Unqork environment. You'll enter this service name in Unqork's PrivateLink Administration.
Connecting to AWS PrivateLink in Unqork
Now you’re ready to begin connecting Unqork to AWS PrivateLink.
Adding an AWS PrivateLink Service in PrivateLink Administration (In Unqork)
First, you'll create the AWS PrivateLink service in Unqork. Your Unqork application connects to your AWS resource with AWS PrivateLink.
At the top right of the Unqork Designer Platform, click Administration.
Under Integration, click PrivateLink Administration.
Click Add PrivateLink.
In the PrivateLink Service Name field, enter the service name you copied in the Copy the AWS Endpoint Service Name section of this article. The entire service name is required.
Click Add PrivateLink.
Reload the PrivateLink Administration page to confirm it added successfully.
Accept the Endpoint Connection From Unqork (In AWS)
You've set up the AWS PrivateLink Connection in AWS and Unqork. Next, you’ll set up the connection to transfer traffic.
In AWS, go to Endpoint Services.
Select the endpoint you created in the Configure the VPC Endpoint Service and NLB section of this article.
In Endpoint Connections, confirm the connection's state. If Pending, select Accept Endpoint Connection Request from the Actions drop-down.
Creating a Service Using AWS PrivateLink in Services Administration (In Unqork)
With the connection set, you must create a new integration in Services Administration to reach the target resource or service.
At the top-right of the Unqork Designer Platform, click Administration.
Under Integration, click Services Administration. The Services Administration page displays.
Click + Add a Service.The Create New Service modal displays.
In the Service Title* field, enter a title. For example,
My Private API.In the Service Name* field, enter a name. For example,
my-private-api. This value cannot include spaces or special characters.Click Next.
From the Share To setting, choose to share with the environment or a specific workspace.
Click Create. The new service's configuration page displays.
Click Edit.
In the Service Protocol + Host* field, enter the DNS name. If the target resource uses HTTP, use the URL under PrivateLink DNS Name in PrivateLink Administration. For example,
http://vpce-000ca-000m.vpce-svc-000e2.us-east-2.vpce.amazonaws.com.If the target resource uses HTTPS, see the Enabling Private DNS in AWS section of this article. and use the URL configured in your VPC Endpoint Service.
Click Save Changes.
Enabling Private DNS in AWS
To use HTTPS to communicate with an AWS target resource, you must enable Private DNS on your AWS PrivateLink.
You must associate a Private DNS Name with your VPC Endpoint Service using the following documentation: https://docs.aws.amazon.com/vpc/latest/privatelink/configure-endpoint-service.html#associate-private-dns-name.
Navigate to Unqork's PrivateLink Administration.
Next to the relevant PrivateLink, click Enable Private DNS.
Configuring a Plug-In Component to Call the AWS PrivateLink Service
Next, you'll configure a Plug-In component to call your AWS PrivateLink service. You’ll also set up an Initializer component to trigger the Plug-In component.
To learn more about configuring an external API call, view our External APIs article.
How you execute the Plug-In component depends on your use case’s needs. Common approaches include:
Using a Button component to trigger the Plug-In component on button-click.
Using an Initializer component to trigger the Plug-In component on page-load. This option is common when using a remote execute to trigger an API module.
What You Need
For this configuration, you need:
1 API module
1 Initializer component
1 Plug-In component
Configure the Plug-In Component
This Plug-In component will make an external API call to run your AWS PrivateLink service.
In the Module Builder, drag and drop a Plug-In component onto the canvas.
In the Property ID field, enter pluginAWS.
In the Canvas Label Text field, enter
pluginAWS.From the Service Type drop-down, select External.
From the External Services drop-down, enter or select your AWS Private Link service .
Complete the Data Source URL value based on the AWS resource.
From the Request Type drop-down, select an API method. The Request Type is based on the action you're performing.
Complete the Inputs table.
Your inputs are based on your AWS resource.
To learn more about configuring a Plug-In component’s Inputs table, view our Plug-In component article.
Click Save Component.
Configure the Initializer Component
This Initializer component triggers your the Plug-In component.
Drag and drop an Initializer component onto your canvas, placing it above your Plug-In component.
In the Property ID field, enter initPlugin.
In the Canvas Label Text field, enter
initPlugin.From the Trigger Type drop-down, select an API method.
The appropriate Trigger Type varies based on your use case needs. To trigger the Initializer component on page-load, select
New SubmissionorEdit Submission. New Submission triggers on page-load when no submission is present. Edit Submission triggers on page-load when a submission is present.In the Outputs table, enter the following:
Source
Type
Value
1
pluginAWS
Trigger
GO
Click Save Component.
Save your module.
You successfully created an AWS PrivateLink connection between Unqork and your AWS resource.