Because API (application programming interface) calls involve exchanging data, they often require authentication. This authentication helps ensure that only those who should be calling an API can call it. Let’s take a closer look at how API authentication works.
Authentication Versus Authorization
Authentication and authorization are two concepts that work together to determine user permissions. While quite similar, authentication and authorization are both necessary parts of the equation. Authentication is the act of verifying a user's identity. Authorization is the act of allowing a user to perform certain actions. You can think of each of these concepts as your application asking a question:
Authentication: Who are you?
Authorization: What can you do?
Think about how you’d access an office building. Most often, you wouldn’t gain access without showing some sort of credentials. And from there, those credentials might only get you access to certain parts of the building.
For authorization, you can customize permissions for each role in your environment. You'll use role-based access control (RBAC) to manage that. You can read more on RBAC and user permissions in our Role Administration article.
Authentication in Unqork works more on a global level, though. So, let's take a closer look at the topic.
Authentication Methods
Almost every API has an authentication need. Some are as simple as requiring a username and password. Others involve generating specific authentication tokens. Each API that you use will have its own set of requirements. Here are some of the most common authentication methods:
Method | Description |
|---|---|
Basic Authentication | Requires only a username and password encoded with base64 sent in the API request header. This is the most straightforward method but the least secure. |
Bearer Authentication | Requires a security token included in the API authorization header. This token, a "bearer token," is usually generated by the server in response to a login request. |
API Keys | A unique value assigned to specific applications or users to prove their identity. This method is usually only used to identify an application, not a user. |
OAuth 2.0 | Involves an authentication flow that begins when a user logs into a system. The system then sends an authentication request back to the user. The user then forwards the request to an authentication server. Finally, the server either rejects authentication or allows it. If allowed, the server returns an access token. |
Of these methods, OAuth 2.0 is the most secure. It’s also the most flexible, allowing a user to get an access token in several ways called "grant types." This is how Unqork authenticates calls made to our internal API.
Authentication in Unqork
Only authenticated users can make calls to the Unqork API. When logged into Unqork, you're already a verified user. And as a verified user, you're authenticated to call the Unqork API. But if you want to make Unqork API calls externally, you'll have to authenticate first. This includes situations involving third-party integrations or API testing tools.
For unverified users, Unqork uses OAuth 2.0 for authentication. We make use of the Password grant type. This type relies on username/password combinations for each user accessing the environment.
To enable the Password grant in your environment:
Click the Administration tab at the top right side of the page.
Under Environment, click Environment Administration.
Under Unqork API, check the Enable OAuth2 Password Grant box.
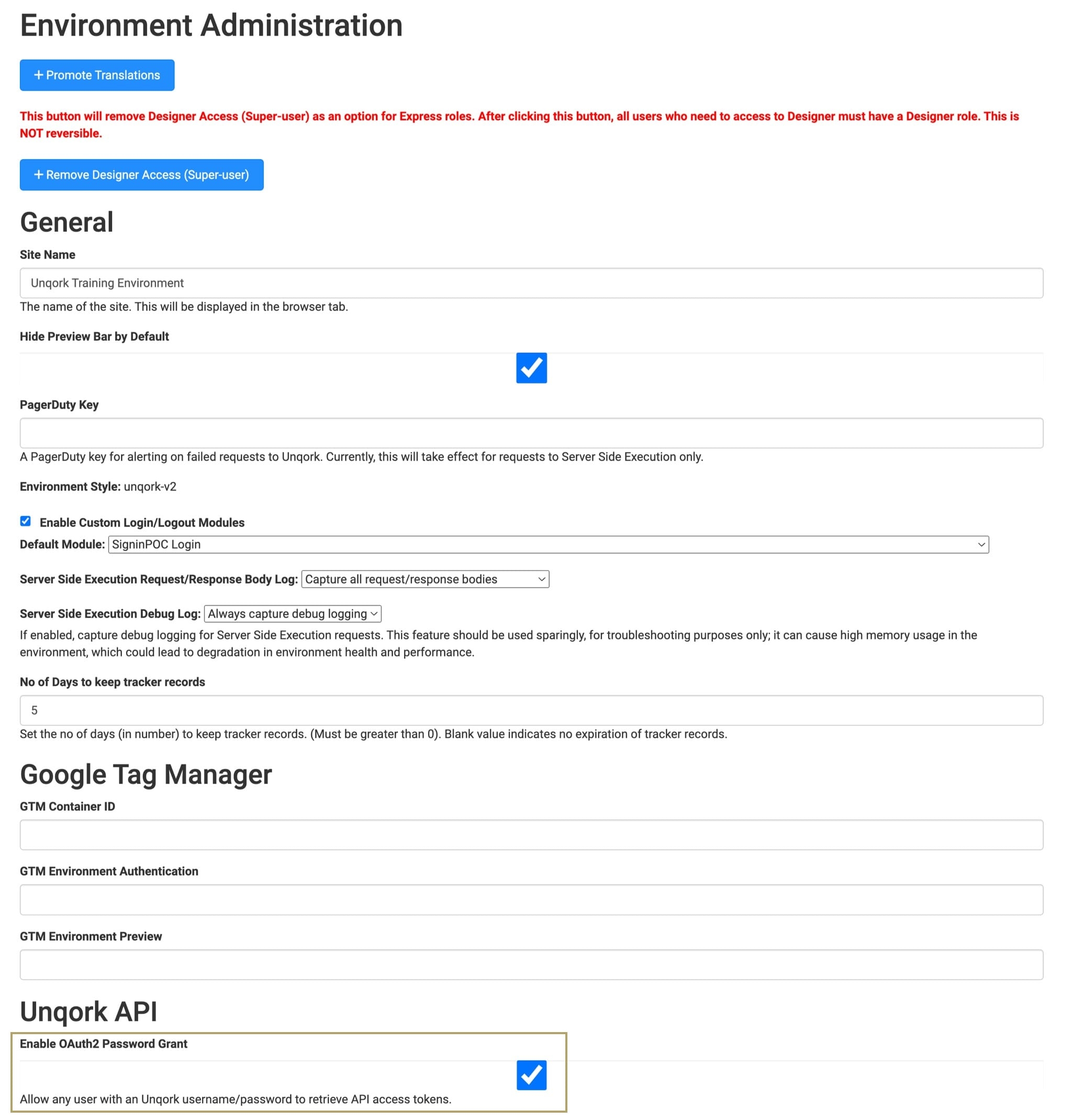
Click Save Changes.