Setting Up Amazon Cognito for SSO in Express View (OIDC)
Overview
In this article, you'll learn how to use Amazon Web Services' Amazon Cognito service as an SSO (single sign-on) provider, using the OIDC (OpenID Connect) authentication method. Amazon Cognito acts as the OP (OpenID Provider) and Unqork is the RP (Relying Party). You'll set up your OIDC configuration on Unqork's Single Sign-On (SSO) Management page.
You can set up SSO configurations for:
-
Express View access: For authentication into the front-end of an application in your environment.
-
Designer access: For authentication in your Unqork environment, known as Designer.
This article shows you how to set up a OIDC configuration using Amazon Cognito as the SSO provider in Express View.
To connect Amazon Cognito to your Unqork application as an SSO provider, your Amazon Cognito administrator needs to set up your application as a new app in a user pool. To learn more, see the Amazon Cognito documentation Getting Started with User Pools here: https://docs.aws.amazon.com/cognito/latest/developerguide/getting-started-with-cognito-user-pools.html.
What You'll Learn
In this article, you'll learn:
-
How OIDC configuration settings map between Amazon Cognito and Unqork.
-
How to set up Amazon Cognito as an OIDC configuration from the Single Sign-On (SSO) Management page.
How Settings Map Between Amazon Cognito and Unqork
| # | Unqork Setting | Related Amazon Cognito Setting |
|---|---|---|
|
1 |
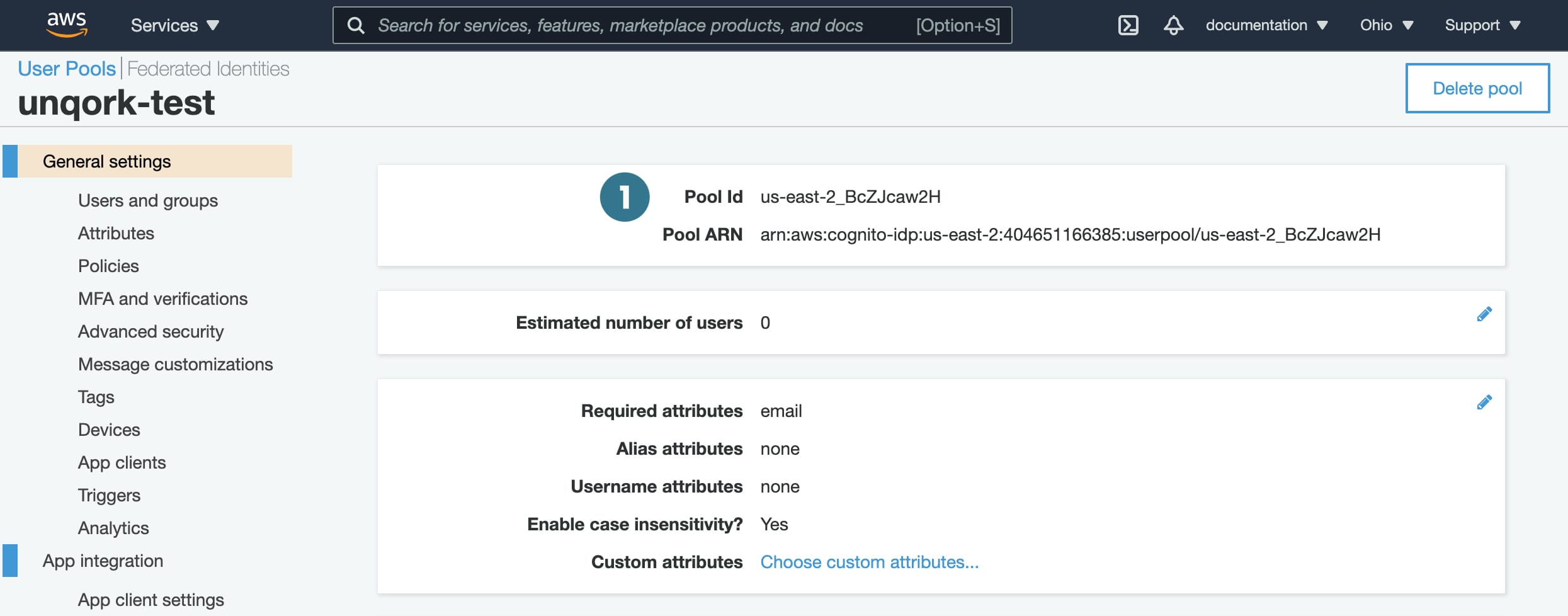
OIDC OP Discover URL/Issuer |
Pool ID The Pool ID alone doesn't work as an OIDC OP Discovery URL/Issuer. But you need the Pool ID to fill in the field on Unqork's end. |
|
2 |
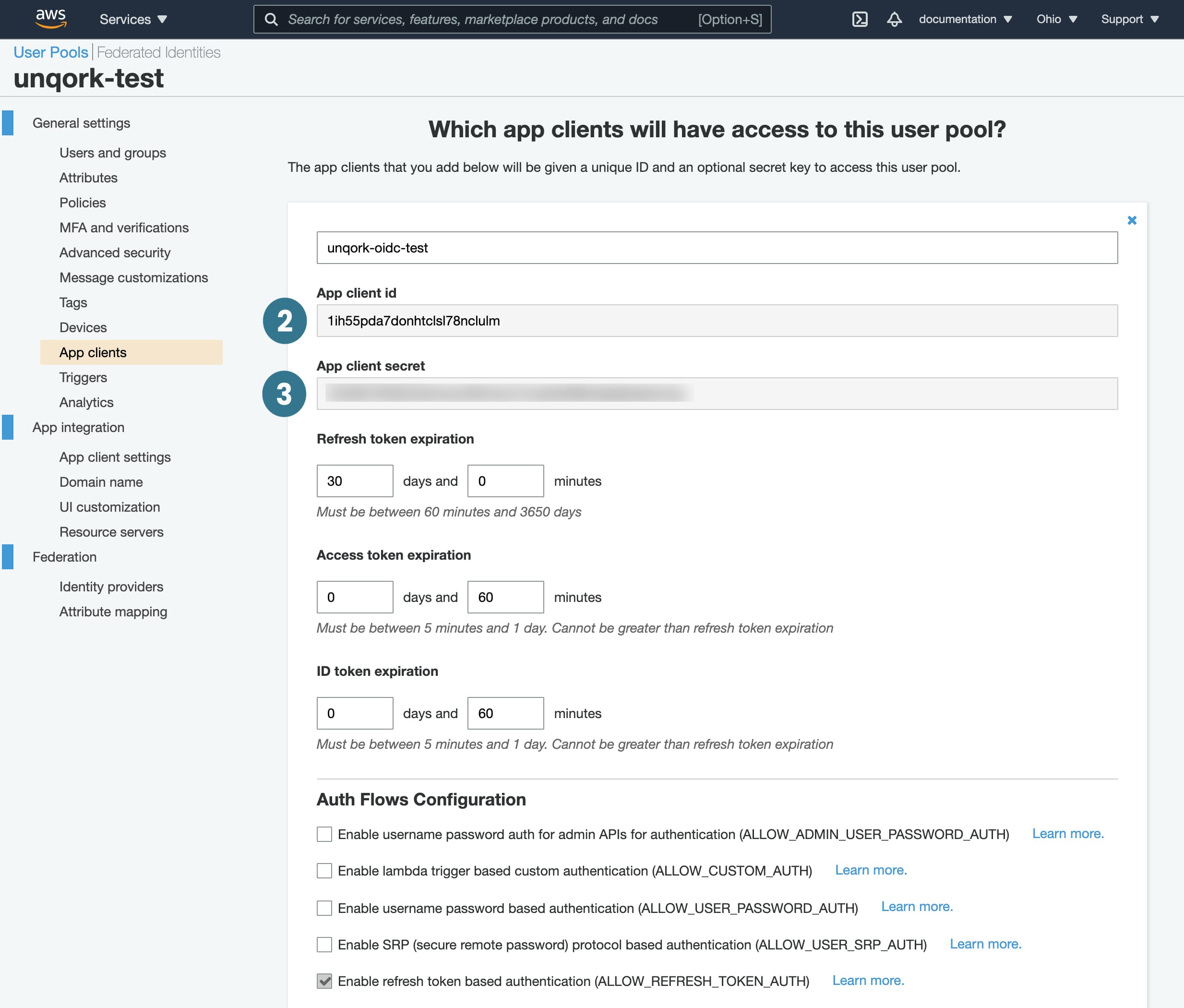
OIDC OP Client ID |
App Client ID |
|
3 |
OIDC OP Client Secret |
App Client Secret |
|
4 |
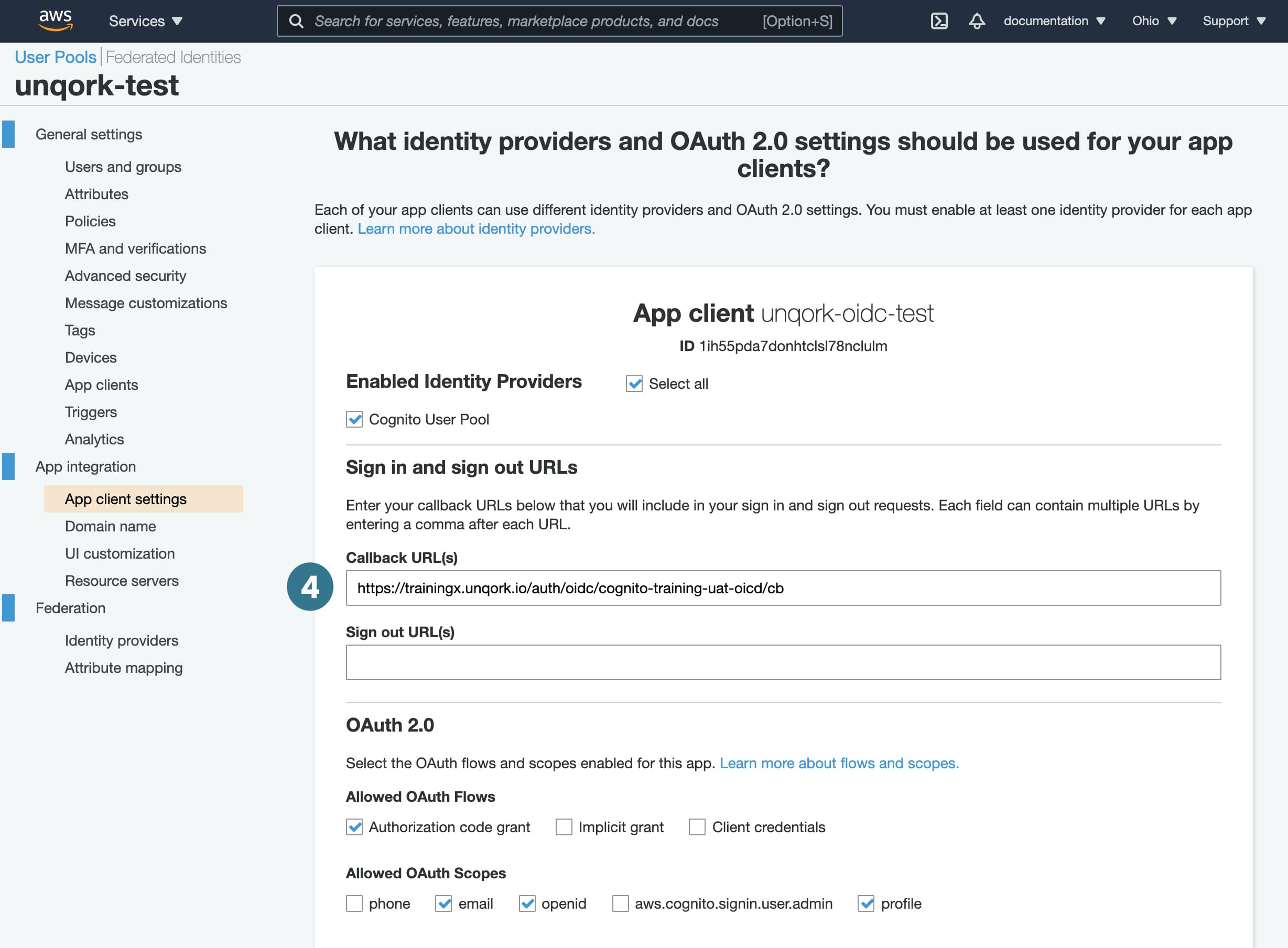
Redirect URI |
Callback URL(s) |
|
5 |
|
Domain Name This setting has no related setting in Unqork. However, you must complete a Domain Name for your configuration to work. The Domain Name doesn't need to correspond to any value used on Unqork's end. |
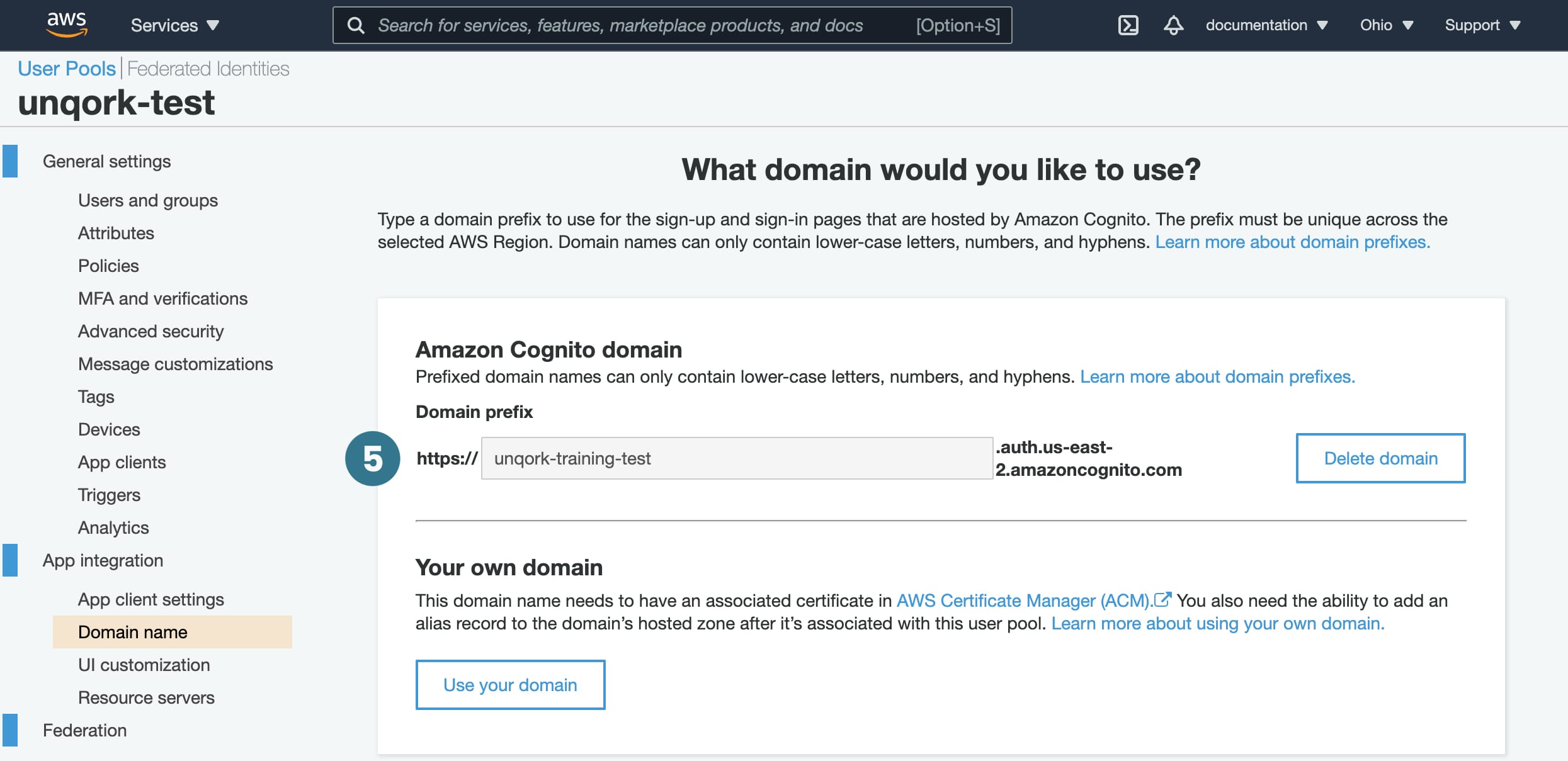
Setting Up Amazon Cognito as an OIDC Configuration in Environment Administration
This is a step-by-step walkthrough of how to set up Amazon Cognito as an OIDC configuration. This is one example of how you might configure Amazon Cognito for SSO in Express View. This approach ensures Amazon Cognito is the single source of truth for your end-user's permissions.
To learn more about all the OIDC configuration settings in Environment Administration, visit our OpenID Connect (OIDC) article. To learn more about using the Single Sign-On (SSO) Management dashboard, view our Single Sign-On (SSO) Management article.
What You Need
For this sample configuration, you need the following information:
-
The Pool ID.
-
The App Client ID.
-
The App Client Secret.
-
A list of scopes to request access to.
-
A list of claims to map to Unqork attributes.
Your specific values for each setting vary based on your use case. Work with the Amazon Cognito administrator to ensure both sides are clear on what information your application needs to access.
To add an OIDC configuration to your environment:
Start the Configuration
| 1. | At the top right of the Unqork Designer Platform, click the Settings drop-down. |
| 2. | Click Administration. |
| 3. | Under Environment, select Single Sign-On (SSO). |
| 4. | Click + New SSO. |
| 5. | From the + New SSO drop-down, select Express. |
Basic Information Tab
The Basic Information tab is the first tab you see when the New Express SSO configuration modal opens. In this tab, you name your configuration and assign end-user permissions.
To add basic information to your OIDC configuration:
| 1. | In the SSO Name field, enter a unique name for your configuration. |
| 2. | From the Default Role drop-down, select a role. |
When setting up SSO for Express View, select a default role with the lowest-level permissions. This lets you rely on the value stored in Amazon Cognito to determine higher-level permissions.
| 3. | From the Default Groups list, select one or more groups. |
Adding Default Groups is optional. By default, no groups are selected.
| 4. | Click Next. |
You progress from the Basic Information tab to the Configure Protocol tab.
Configure Protocol Tab
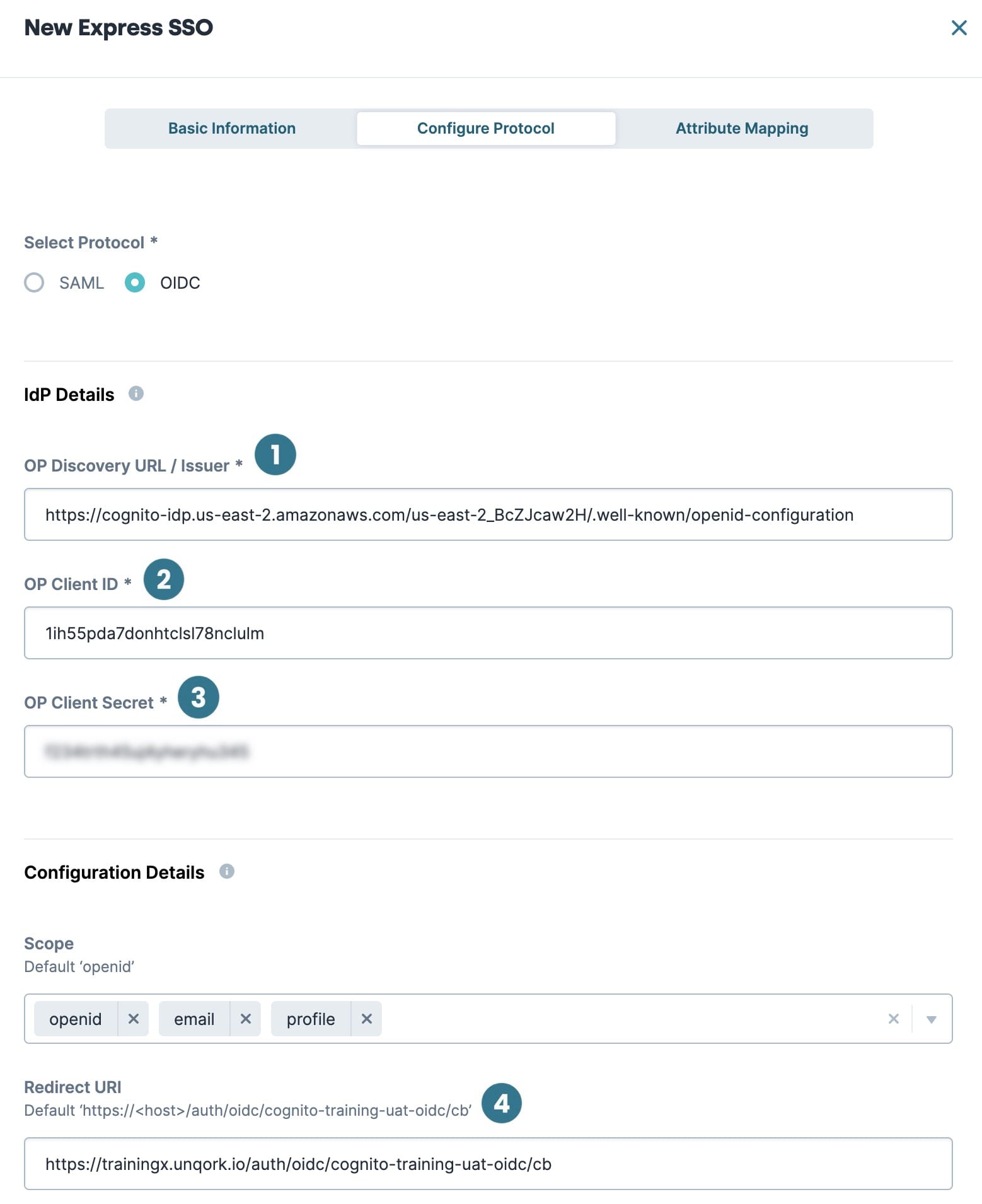
Now, select the OIDC protocol from the Configure Protocol tab and set up the OIDC configuration. These settings are fairly standard and tend to have predictable values regardless of your use case. However, be mindful of listing the appropriate scopes to give you access to the necessary claims in the JWT.
| 1. | Select OIDC as the Protocol. |
| 2. | In the OIDC OP Discovery URL/Issuer field, enter https://cognito-idp.<region>.amazonaws.com/<pool ID>/.well-known/openid-configuration. |
| 3. | In the OIDC OP Discovery URL/Issuer field, replace <region> with your AWS region, and <pool ID> with the Pool ID. |
| 4. | In the OP Client ID field, enter your Client ID. |
| 5. | In the OP Client Secret field, enter your Client Secret. |
| 6. | From the Scope field, select or enter a scope. If the scope you want isn't in the default drop-down, type the scope in the Scope field and press Enter/Return or select Create {scope name}. You can add as many scopes as you want. |
The default scope value is openid. But, it's best practice to still select openid in the Scope field.
The profile scope typically acts as the Amazon Cognito profile, and contains associated key information. By default, the profile scope contains basic information about the user. But, the profile scope can include a more complex list of custom claims as well.
| 7. | In the Redirect URI field, enter your environment-specific Redirect URI. In most cases, your value looks like this: https://<host>/auth/oidc/<OIDCname>/cb, where <host> is the name of your environment and <OIDCname> is the name of your OIDC configuration. |
The Redirect URI in Unqork must match the Sign-In Redirect URI in Amazon Cognito.
Be sure to use the Express View-specific host value. For example unqork-uatx.unqork.io, not unqork-uat.unqork.io.
| 8. | Click Next. |
You progress from the Configure Protocol tab to the Attribute Mapping tab.
The Configure Protocol tab has several advanced settings you can enable. To access these settings, click Show Advanced Settings. Whether or not you need to adjust these settings depends on your use case. For this Amazon Cognito configuration, using any Advanced Settings is not required. Visit our OpenID Connect (OIDC) article for more information.
Attribute Mapping Tab
Next, map claims in the JWT sent by the OP to Unqork attributes in the session's currentUser object. For example, mapping the OP-provided email address to the Unqork attribute email.
You can create dynamic, conditional, or static attribute mappings. See the Creating Attribute Mappings section in our OpenID Connect (OIDC) article for more information and detailed examples.
To add an attribute mapping:
By default, the Attribute Mapping tab includes the mapping {{sub}} to userId. Do not delete this mapping or your SSO configuration can fail.
| 1. | Click + Add Attribute Mapping. |
| 2. | Complete the OIDC Claim side of the mapping. |
| 3. | From the Unqork Attribute drop-down, select a default Unqork attribute. Or, enter the attribute's name in the Unqork Attribute field then press Enter/Return or select Create {scope name}. |
| 4. | Repeat the above steps as needed. |
User Management
These user management settings are more variable and highly dependent on your unique use case. However, in this configuration Amazon Cognito is the single source of truth for authentication. This means the user doesn't need to exist in Unqork, as Unqork isn't acting as the user management system. So, consider the following settings:
| 1. | Click Show User Management. |
| 2. | Verify Disable New User Creation is selected. |
| 3. | Click Create SSO. |
Verify the SSO configuration in Environment Administration matches the SSO configuration in Single Sign-On (SSO) Management. If you are encountering issues, visit the Troubleshooting Tips section below.
Your SSO configuration is now complete. The configuration modal closes and returns your focus to the Single Sign-On (SSO) Management dashboard.
Testing Your Configuration
You're ready to test your configuration.
You need a set of test credentials from the Amazon Cognito administrator. The test user must be assigned to the app integration in Amazon Cognito, under the Users and Groups tab.
| 1. | At the top right of the Unqork Designer Platform, click the Settings drop-down. |
| 2. | Click Administration. |
| 3. | Under Environment, select Single Sign-On (SSO). |
| 4. | In the SSO dashboard, find the SSO configuration to preview. |
| 5. | Under the Actions column, click Manage. |
| 6. | From the Manage drop-down, right-click Preview. |
| 7. | Click Open Link in Incognito Window. |
| 8. | Paste the Unqork entrypoint URL into the browser. |
By default, the Unqork Entrypoint URL uses 123 as the module ID. To test access to an actual module in your application, replace 123 at the end of the URL with your module's module ID.
| 9. | Log in using your test credentials. |
If you see an error page, there are issues with your configuration. If you can successfully log in to Unqork, your OIDC configuration of Amazon Cognito as SSO provider is complete.
Troubleshooting Tips
Understanding what's causing an error is one of the most frustrating parts of creating a new configuration. One of the most common sources of error is not using the Express View-specific host value in the OIDC Redirect URI field. Not adding a domain name to your app integration can also cause your configuration to fail. See the How Settings Map Between Amazon Cognito and Unqork section for an image of where to find the Domain Name tab in Amazon Cognito.

